暗号化
Capgoは、アプリバンドルに対する堅牢なエンドツーエンド暗号化を提供し、JavaScriptコードとアセットが送信と保存中に保護されることを保証します。この暗号化システムは、ライブアップデートの利便性を維持しながら、アプリのセキュリティを完全に制御できるように設計されています。
Capgoの暗号化システムは、業界標準の暗号化方式を使用して、バンドルを不正アクセスから保護します。暗号化が有効になっている場合、バンドルは開発環境を離れる前に暗号化され、ユーザーのデバイス上のアプリによって復号化されるまで暗号化されたままになります。
真のエンドツーエンド暗号化: アップデートに署名するだけ(コードが公開的に読み取り可能)の他のOTAアップデートプラットフォームとは異なり、Capgoは真のエンドツーエンド暗号化を提供します。これは、ユーザーのみがアップデートを復号化でき、Capgo自体を含む他の誰もできないことを意味します。バンドルコンテンツは、配信プロセス全体を通じて完全にプライベートで読み取り不可能なままです。
暗号化の仕組み
Section titled “暗号化の仕組み”Capgoは、最適なセキュリティとパフォーマンスのためにRSAとAES暗号化を組み合わせたハイブリッド暗号化アプローチを使用します:
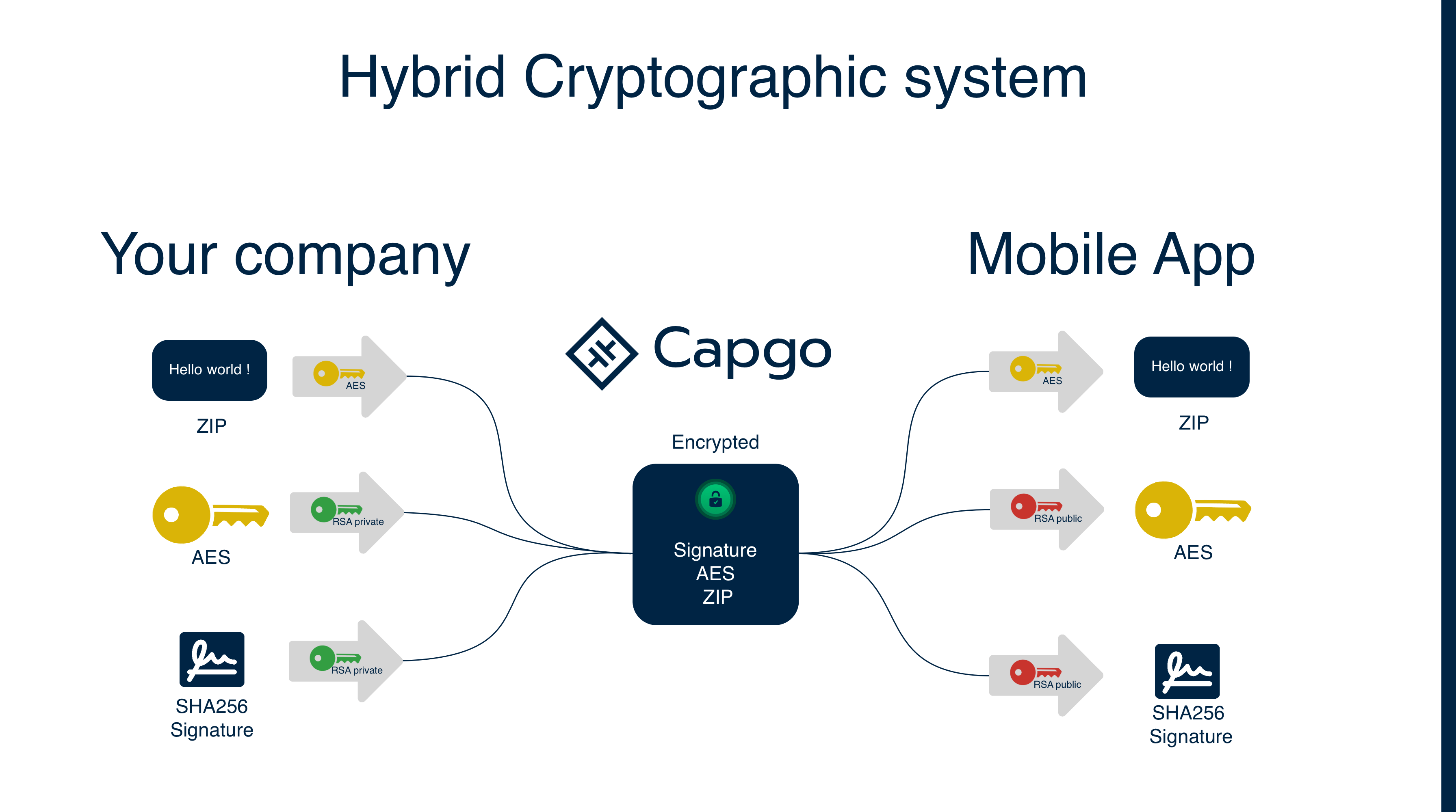
1. 鍵生成
Section titled “1. 鍵生成”- プライベートキー: 開発環境で生成され、安全に保存されます(暗号化に使用)
- パブリックキー: プライベートキーから派生し、アプリのCapacitor configに保存されます(復号化に使用)
- セッションキー: 各バンドルアップロードに対してランダムなAESキーが生成されます
2. 暗号化プロセス
Section titled “2. 暗号化プロセス”- 各バンドルアップロードに対してランダムなAESセッションキーが生成されます
- バンドルはAESセッションキーを使用して暗号化されます
- バンドルチェックサムが計算されます
- AESセッションキーとチェックサムの両方がRSAプライベートキーを使用して一緒に暗号化されます(「署名」を作成)
- 暗号化されたバンドルと暗号化された署名が保存されます
チェックサムはAESキーと一緒に暗号化されて改ざんを防ぎます。RSAプライベートキーのみがこの署名を作成でき、対応するパブリックキーのみがそれを復号化できるため、AESセッションキーと予期されるチェックサムの両方が真正であり、攻撃者によって変更されていないことが保証されます。
3. 復号化プロセス
Section titled “3. 復号化プロセス”- アプリは暗号化されたバンドルと暗号化された署名をダウンロードします
- Capgo SDKは、RSAパブリックキー(アプリに保存)を使用して署名を復号化します
- これによりAESセッションキーと元のチェックサムが明らかになります
- AESセッションキーを使用してバンドルを復号化します
- 復号化されたバンドルのチェックサムが計算され、整合性検証のために元のチェックサムと比較されます
このプロセスにより、攻撃者が暗号化されたバンドルを傍受しても、AESセッションキーを変更したり偽のチェックサムを提供したりすることはできません。なぜなら、パブリックキーが復号化できる有効な署名を作成するには、プライベートキーが必要だからです。
Capgoと他のプラットフォームの比較
Section titled “Capgoと他のプラットフォームの比較”| 機能 | Capgo | 他のOTAプラットフォーム |
|---|---|---|
| バンドルコンテンツ | 完全に暗号化(読み取り不可能) | 公開的に読み取り可能 |
| セキュリティ方式 | 真のエンドツーエンド暗号化 | コード署名のみ |
| プライバシーレベル | ゼロノレッジ(Capgoでさえコードを読めない) | プラットフォームがコードにアクセス可能 |
| 保護 | コンテンツ + 整合性 + 真正性 | 整合性 + 真正性のみ |
なぜこれが重要か:
- コード署名は、アップデートが改ざんされておらず、正しいソースから来ていることを検証するだけです
- エンドツーエンド暗号化は、実際のコードコンテンツが送信と保存中にプライベートで読み取り不可能なままであることを保証します
- Capgoの真のエンドツーエンド暗号化により、ユーザーのみがアップデートを復号化でき、Capgo自体を含む他の誰もできません
Capgoは暗号化V2を標準暗号化方式として使用します:
暗号化V2(現在の標準)
Section titled “暗号化V2(現在の標準)”- セキュリティ強化のためRSA-4096を使用
- 認証付き暗号化のためAES-256-GCM
- 整合性検証を提供
- より優れたパフォーマンスとセキュリティ
暗号化V1(非推奨)
Section titled “暗号化V1(非推奨)”- 鍵暗号化にRSA-2048を使用
- バンドル暗号化にAES-256-CBC
- 現在のCLIでは利用できません
- V1を使用しているレガシーアプリはV2に移行する必要があります
暗号化の設定
Section titled “暗号化の設定”ステップ1: 暗号化キーの生成
Section titled “ステップ1: 暗号化キーの生成”まず、Capgo CLIを使用して暗号化キーを生成します:
# 新しい暗号化キーを生成(現在のディレクトリにファイルを作成)npx @capgo/cli@latest key createこれにより以下が作成されます:
.capgo_key_v2: プライベートキー(これを安全に保管してください!).capgo_key_v2.pub: パブリックキー(アプリで使用)
これらのファイルは、コマンドを実行した現在のディレクトリに作成されます。
ステップ2: Capacitor Configにパブリックキーを保存(必須)
Section titled “ステップ2: Capacitor Configにパブリックキーを保存(必須)”モバイルアプリがバンドルを復号化できるように、パブリックキーをCapacitor configに保存する必要があります:
# ファイルからCapacitor configにパブリックキーを保存(必須)npx @capgo/cli@latest key save --key ./.capgo_key_v2.pub
# またはパブリックキーデータを直接保存npx @capgo/cli@latest key save --key-data "$CAPGO_PUBLIC_KEY"ステップ3: Capacitorプラットフォームを同期(必須)
Section titled “ステップ3: Capacitorプラットフォームを同期(必須)”パブリックキーを保存した後、更新されたconfigをネイティブレイヤーにコピーするためにCapacitorプラットフォームを同期する必要があります:
# プラットフォームを同期してconfigをネイティブにコピーnpx cap syncバンドルの暗号化
Section titled “バンドルの暗号化”方法1: アップロード時に暗号化
Section titled “方法1: アップロード時に暗号化”最も簡単な方法は、アップロードプロセス中に暗号化することです:
# 自動暗号化でアップロードnpx @capgo/cli@latest bundle upload --key-v2
# 外部ストレージの場合、最初に暗号化する必要があります(下記の手動暗号化ワークフローを参照)方法2: 手動暗号化ワークフロー
Section titled “方法2: 手動暗号化ワークフロー”より詳細な制御のために、バンドルを手動で暗号化できます:
-
zipバンドルを作成:
Terminal window npx @capgo/cli@latest bundle zip com.example.app --path ./dist --key-v2 -
バンドルを暗号化:
Terminal window npx @capgo/cli@latest bundle encrypt ./com.example.app.zip CHECKSUM_FROM_STEP_1 -
ストレージにアップロード(例:S3)してCapgoに登録:
Terminal window # まず暗号化されたバンドルをストレージにアップロード(例:AWS S3)aws s3 cp ./encrypted-bundle.zip s3://your-bucket/encrypted-bundle.zip# 次に外部URLを使用してCapgoに登録npx @capgo/cli@latest bundle upload --external https://your-storage.com/encrypted-bundle.zip --iv-session-key IV_SESSION_KEY_FROM_STEP_2
キーの安全な保存
Section titled “キーの安全な保存”プライベートキーのオプション:
-
ファイルベース(ローカル開発):
Terminal window # プロジェクトルートに.capgo_key_v2ファイルとして保存npx @capgo/cli@latest bundle upload --key-v2 -
環境変数(CI/CD):
Terminal window # CI用に環境変数に保存export CAPGO_PRIVATE_KEY="$(cat .capgo_key_v2)"npx @capgo/cli@latest bundle upload --key-data-v2 "$CAPGO_PRIVATE_KEY"
パブリックキーのセットアップ(必須):
# モバイルアプリ用にCapacitor configにパブリックキーを保存する必要がありますnpx @capgo/cli@latest key save --key ./.capgo_key_v2.pub本番環境:
- 安全なキー管理サービス(AWS KMS、Azure Key Vaultなど)にプライベートキーを保存
- プライベートキーにはCI/CDシークレット管理を使用
- プライベートキーをバージョン管理にコミットしない
キーの使用:
- プライベートキー: バンドルアップロード時の暗号化にCLIが使用(安全に保管)
- パブリックキー: デバイス上の復号化のためアプリ構成に保存(コミット可)
キーのローテーション
Section titled “キーのローテーション”セキュリティ強化のために暗号化キーを定期的にローテーション:
-
新しいキーを生成:
Terminal window # まず目的のディレクトリに移動してから、キーを作成mkdir ./new-keys && cd ./new-keysnpx @capgo/cli@latest key create -
新しいパブリックキーをCapacitor configに保存:
Terminal window npx @capgo/cli@latest key save --key ./new-keys/.capgo_key_v2.pub -
アプリ構成を新しいパブリックキーで更新
-
新しいキーで暗号化されたバンドルをアップロードする前に、更新されたアプリをデプロイ
セキュリティのベストプラクティス
Section titled “セキュリティのベストプラクティス”キーのセキュリティ
Section titled “キーのセキュリティ”- プライベートキーを共有しない(環境間やチームメンバー間で)
- 異なるキーを使用(異なる環境用:dev、staging、production)
- 定期的にキーをローテーション(推奨:6〜12ヶ月ごと)
- 適切なキー管理システムを使用してキーを安全に保存
バンドルのセキュリティ
Section titled “バンドルのセキュリティ”- 常に検証(復号化後のバンドル整合性)
- 監視(異常なダウンロードパターンや失敗)
- HTTPSを使用(すべてのバンドルURL用、モバイルアプリで必須)
- 適切なエラー処理を実装(復号化失敗用)
アクセス制御
Section titled “アクセス制御”- アクセスを制限(承認された担当者のみに暗号化キーへのアクセス)
- ロールベースのアクセスを使用(キー管理操作用)
- 定期的に監査(キーの使用とアクセス)
- 適切なバックアップとリカバリー手順を実装
暗号化のトラブルシューティング
Section titled “暗号化のトラブルシューティング”一般的な問題
Section titled “一般的な問題”復号化失敗:
- プライベートキーが暗号化に使用されたパブリックキーと一致することを確認
ivSessionKeyが正しいことを確認- 暗号化V2を使用していることを確認(V1はサポートされていません)
キー関連のエラー:
- プライベートキーの形式が正しいことを確認(PEM形式)
- キーが保存/転送中に破損していないことを確認
- アプリ構成でキーが適切な権限を持っていることを確認
パフォーマンスの問題:
- 大きなバンドルは暗号化/復号化に時間がかかる場合があります
- バンドルサイズを削減するために差分アップデートの使用を検討
- 復号化中のデバイスパフォーマンスを監視
デバッグコマンド
Section titled “デバッグコマンド”暗号化ステータスを確認:
npx @capgo/cli@latest app debug暗号化/復号化ワークフローをテスト:
# 完全なワークフローをテスト:zip → 暗号化 → 復号化 → 解凍npx @capgo/cli@latest bundle zip com.example.app --key-v2npx @capgo/cli@latest bundle encrypt ./com.example.app.zip CHECKSUM --jsonnpx @capgo/cli@latest bundle decrypt ./encrypted-bundle.zip IV_SESSION_KEYコンプライアンスと標準
Section titled “コンプライアンスと標準”Capgoの暗号化実装は業界標準に従います:
- AES-256: FIPS 140-2承認の暗号化アルゴリズム
- RSA-4096: キー保護のための強力な非対称暗号化
- GCMモード: 機密性と真正性の両方を提供
- セキュアランダム: 暗号学的に安全な乱数生成
これにより、Capgoは以下への準拠が必要なアプリケーションに適しています:
- GDPR(一般データ保護規則)
- HIPAA(医療保険の携行性と責任に関する法律)
- SOC 2(サービス組織管理2)
- ISO 27001(情報セキュリティマネジメント)
パフォーマンスに関する考慮事項
Section titled “パフォーマンスに関する考慮事項”暗号化のオーバーヘッド
Section titled “暗号化のオーバーヘッド”- バンドルサイズ: 暗号化されたバンドルはわずかに大きくなります(約1〜2%のオーバーヘッド)
- 処理時間: 暗号化/復号化は最小限の遅延を追加
- メモリ使用量: 暗号化/復号化操作中の一時的な増加
最適化のヒント
Section titled “最適化のヒント”- 暗号化されたデータ転送を最小化するために差分アップデートを使用
- 画像をWebP形式に変換してバンドルサイズを最適化
- バンドル化前にJavaScriptとCSSファイルを最小化
- 未使用の依存関係とコードを削除
- 古い/遅いデバイスでデバイスパフォーマンスを監視
