组织安全
Capgo提供全面的安全控制,使组织管理员能够对所有成员执行安全策略。这些功能帮助您满足合规要求、保护敏感数据并保持强大的安全态势。
组织安全设置允许超级管理员配置:
- 双因素认证(2FA)强制执行 - 要求所有成员启用2FA
- 密码策略 - 设置密码复杂性要求
- API密钥安全 - 强制执行安全的API密钥和过期策略
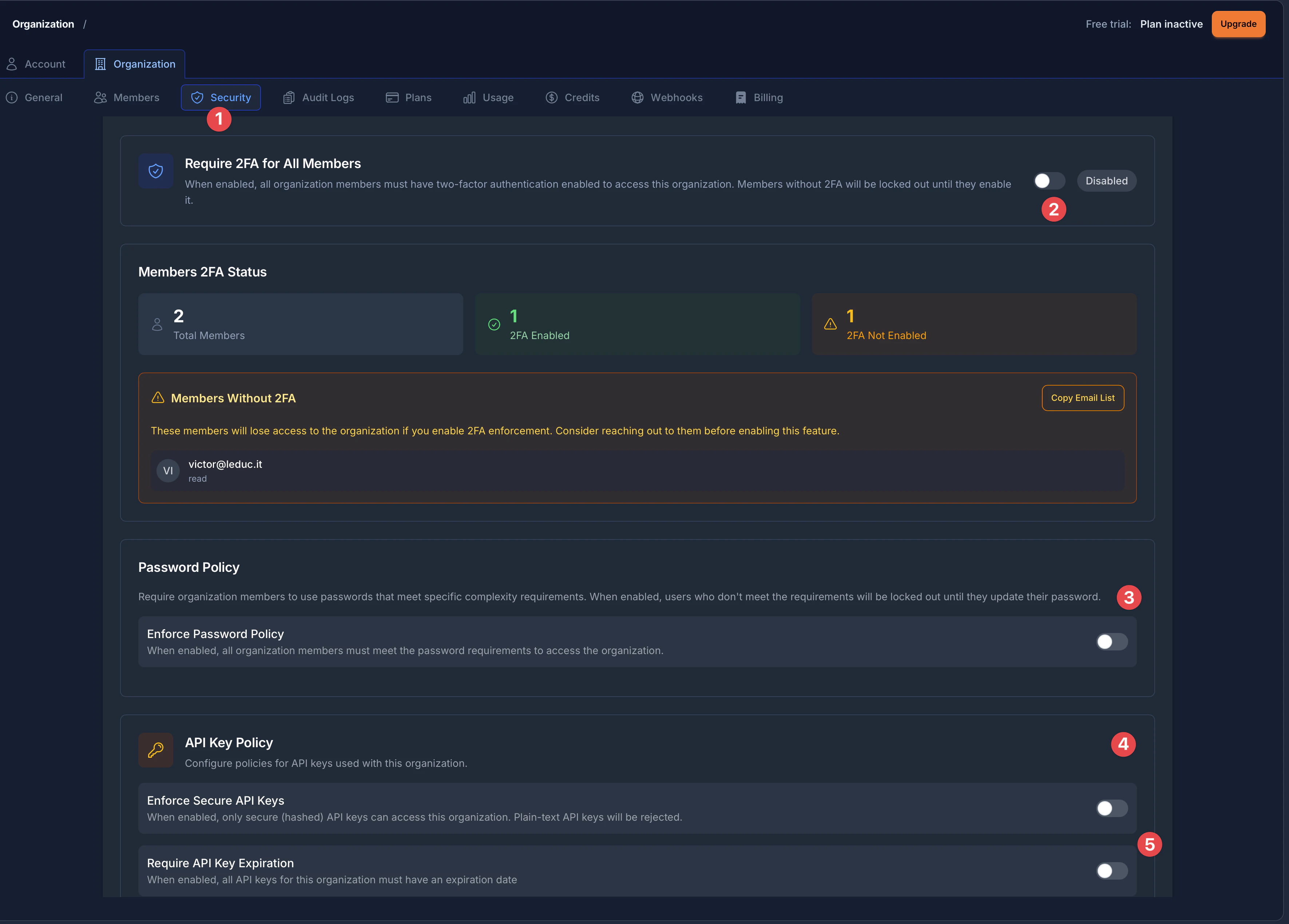
安全页面被组织成清晰标记的部分:
- 安全选项卡 - 从组织设置侧边栏访问所有安全设置
- 2FA强制执行 - 双因素认证要求的开关和状态显示
- 密码策略 - 为组织成员配置密码复杂性规则
- API密钥策略 - 安全API密钥和过期要求的设置
- API密钥过期 - 控制API密钥是否必须有过期日期
访问安全设置
Section titled “访问安全设置”- 点击侧边栏中的设置导航到您的组织设置
- 点击设置页面顶部的组织选项卡
- 从组织导航栏选择安全选项卡(用盾牌图标高亮显示)
双因素认证(2FA)强制执行
Section titled “双因素认证(2FA)强制执行”2FA强制执行要求所有组织成员在其账户上启用双因素认证。这通过要求密码和验证码来添加关键的安全层。
强制执行2FA时会发生什么
Section titled “强制执行2FA时会发生什么”- 没有2FA的成员将被立即阻止访问组织应用
- Web仪表板和CLI都会执行此要求
- 新成员必须在访问组织资源之前启用2FA
- 系统实时跟踪哪些成员已启用2FA
了解2FA状态面板
Section titled “了解2FA状态面板”安全页面显示一个全面的成员2FA状态面板,显示:
- 总成员数 - 您组织中的成员总数
- 2FA已启用(绿色指示器)- 已成功启用双因素认证的成员
- 2FA未启用(橙色警告指示器)- 仍需设置2FA的成员
当成员未启用2FA时,他们会出现在未启用2FA的成员警告框中。此框显示:
- 每个成员的电子邮件地址及其在组织中的角色
- 复制邮件列表按钮,用于快速复制所有受影响的电子邮件地址以进行沟通
启用2FA强制执行
Section titled “启用2FA强制执行”- 导航到组织设置 > 安全
- 在页面顶部找到要求所有成员启用2FA部分
- 查看成员2FA状态面板以了解哪些成员将受到影响
- 如果有成员没有2FA,在启用之前使用复制邮件列表按钮通知他们
- 切换要求所有成员启用2FA旁边的开关以启用强制执行
- 开关将在右侧显示已禁用或已启用状态
2FA强制执行的CLI支持
Section titled “2FA强制执行的CLI支持”您也可以通过CLI管理2FA强制执行:
# 启用2FA强制执行npx @capgo/cli organization set YOUR_ORG_ID --enforce-2fa
# 禁用2FA强制执行npx @capgo/cli organization set YOUR_ORG_ID --no-enforce-2fa
# 检查成员2FA状态npx @capgo/cli organization members YOUR_ORG_ID有关2FA强制执行的详细信息,请参阅2FA强制执行指南。
密码策略允许您为所有组织成员强制执行密码复杂性要求。当成员的密码不符合策略要求时,他们必须更新密码才能访问组织资源。
密码策略部分(在概览图像中用指示器3标记)提供了一个简单的开关来在整个组织中强制执行密码要求。
密码策略如何工作
Section titled “密码策略如何工作”当您启用密码策略时:
- 所有组织成员必须满足密码复杂性要求
- 不符合要求的用户将被锁定,直到他们更新密码
- 该策略适用于所有成员,无论其角色如何
启用密码策略
Section titled “启用密码策略”- 转到组织设置 > 安全
- 向下滚动找到密码策略部分
- 阅读描述:“要求组织成员使用满足特定复杂性要求的密码”
- 切换强制执行密码策略开关以启用它
- 开关描述说明:“启用后,所有组织成员必须满足密码要求才能访问组织”
可用的密码要求
Section titled “可用的密码要求”| 设置 | 描述 | 范围 |
|---|---|---|
| 最小长度 | 所需的最小字符数 | 6-128个字符 |
| 要求大写字母 | 密码必须包含至少一个大写字母(A-Z) | 开/关 |
| 要求数字 | 密码必须包含至少一个数字(0-9) | 开/关 |
| 要求特殊字符 | 密码必须包含至少一个特殊字符(!@#$%^&*等) | 开/关 |
成员合规跟踪
Section titled “成员合规跟踪”当密码策略处于活动状态时,您可以监控合规情况:
- 总成员数:组织中的成员数量
- 合规:密码符合策略要求的成员
- 不合规:需要更新密码的成员
不合规的成员会与其电子邮件地址一起列出。您可以复制邮件列表以通知他们有关策略和所需的密码更改。
密码策略最佳实践
Section titled “密码策略最佳实践”- 从合理的要求开始:最少10-12个字符,包含大小写字母和数字,在不过度限制的情况下提供良好的安全性
- 沟通变更:在启用新密码要求之前通知您的团队
- 允许过渡时间:给成员时间更新他们的密码
- 考虑密码管理器:建议团队成员使用密码管理器来生成和存储强密码
API密钥安全
Section titled “API密钥安全”Capgo为API密钥提供两种安全控制:强制执行安全(哈希)API密钥和要求过期日期。API密钥策略部分(在概览图像中用指示器4标记)由钥匙图标标识。
强制执行安全API密钥
Section titled “强制执行安全API密钥”API密钥策略部分的第一个选项是强制执行安全API密钥。启用后,此设置要求组织中的所有API密钥使用安全/哈希格式创建。
哈希API密钥更安全,因为:
- 实际的密钥值永远不会存储在我们的服务器上
- 只有您(和您的系统)可以访问完整的密钥
- 即使我们的数据库被泄露,您的密钥也无法被使用
开关描述说明:“启用后,只有安全(哈希)API密钥才能访问此组织。纯文本API密钥将被拒绝。”
启用安全API密钥
Section titled “启用安全API密钥”- 转到组织设置 > 安全
- 向下滚动找到API密钥策略部分(寻找钥匙图标)
- 找到强制执行安全API密钥开关
- 切换开关以启用安全API密钥强制执行
- 现有密钥不受影响;策略适用于新密钥的创建
API密钥过期策略
Section titled “API密钥过期策略”第二个选项(在概览图像中用指示器5标记)是要求API密钥过期。您可以要求所有API密钥有过期日期,限制其有效期。
这是一种安全最佳实践,可以:
- 限制密钥被泄露时的暴露窗口
- 确保定期密钥轮换
- 帮助满足凭证管理的合规要求
开关描述说明:“启用后,此组织的所有API密钥必须有过期日期”
配置过期策略
Section titled “配置过期策略”- 转到组织设置 > 安全
- 找到API密钥策略部分
- 找到要求API密钥过期开关(在强制执行安全API密钥下方)
- 切换开关以启用过期要求
- 启用后,设置最大过期天数(1-365天)
- 这限制了可以设置的过期日期距离现在有多远
- 例如:设置90天意味着密钥最多可以在创建后90天过期
推荐的API密钥策略
Section titled “推荐的API密钥策略”| 用例 | 安全密钥 | 过期 | 最大天数 |
|---|---|---|---|
| 开发 | 推荐 | 可选 | 30-90 |
| CI/CD管道 | 必需 | 必需 | 90-180 |
| 生产 | 必需 | 必需 | 30-90 |
| 企业/合规 | 必需 | 必需 | 30-60 |
组织安全功能帮助您满足各种合规要求:
| 标准 | 相关功能 |
|---|---|
| SOC 2 | 2FA强制执行、密码策略、API密钥控制 |
| ISO 27001 | 所有安全功能帮助证明访问控制 |
| HIPAA | 强认证和访问管理 |
| GDPR | 通过访问控制实现数据保护 |
| PCI DSS | 多因素认证、强密码 |
监控合规状态
Section titled “监控合规状态”安全仪表板提供以下实时可见性:
- 有多少成员启用了2FA
- 组织中的密码策略合规性
- API密钥安全采用情况
使用”复制邮件列表”功能轻松导出不合规成员列表以进行针对性沟通。
”访问被拒绝:不符合安全策略”
Section titled “”访问被拒绝:不符合安全策略””问题:成员无法访问组织。
解决方案:
- 检查是否强制执行2FA - 成员需要启用2FA
- 检查密码策略是否处于活动状态 - 成员需要更新密码
- 在安全仪表板中验证成员的合规状态
无法启用安全功能
Section titled “无法启用安全功能”问题:安全开关被禁用或没有响应。
解决方案:
- 确保您在组织中拥有super_admin角色
- 检查您的网络连接
- 尝试刷新页面
- 如果问题持续存在,请联系支持
API密钥创建失败
Section titled “API密钥创建失败”问题:无法创建新的API密钥。
解决方案:
- 如果强制执行安全密钥,请确保您使用的是安全密钥创建流程
- 如果要求过期,请在允许的范围内设置过期日期
- 检查最大过期天数设置
